TOTPRadius : Azure AD Proxy mode
The LDAP proxy mode of TOTPRadius was introduced as a workaround for implementing 2FA access for systems without native support for multiple authentication sources. This works perfectly fine for organizations with full on-premises or hybrid Active Directory implementations where domain controllers can be accessed over the local network directly using LDAP protocol.
We are discovering more and more organizations moving to full cloud Azure AD (Microsoft Entra ID) implementation while keeping some services, such as VPN, on-premises. As the LDAP interface of Azure AD (Microsoft Entra ID) is not accessible directly, it was not possible to configure TOTPRadius to use Azure AD (Microsoft Entra ID) as its authentication source.
This is the reason we added a new feature, Azure AD (Microsoft Entra ID) Proxy, which will address this gap. Starting from v0.2.7, TOTPRadius can be configured to use Azure AD (Microsoft Entra ID) as the authentication source.
Use Cases
There may be many use cases for Azure AD (Microsoft Entra ID) Proxy mode to be used. We will list only a few based on our recent experience:
- A customer having no onPrem Active Directory, but wishing to implement Cisco Meraki Client VPN access to their corporate network
- An organization having both onPrem and Azure Active Directory with a remote office with no domain controllers present and wishing to organize access to the network of the remote office via FortiGate VPN
- An organization having both onPrem and Azure Active Directory; with no redundancy for local DC server, wishing to have Azure AD (Microsoft Entra ID) as the backup authentication source for the VPN access (LDAP Proxy and Azure AD (Microsoft Entra ID) Proxy modes can co-exist)
Operating principle
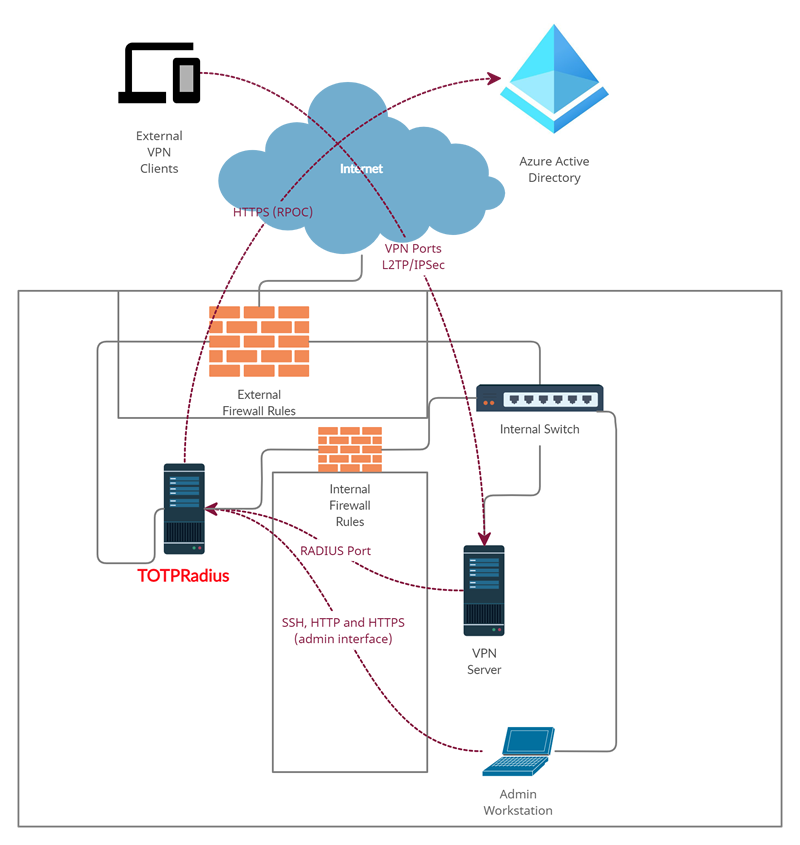
TOTPRadius Azure AD (Microsoft Entra ID) proxy mode is based on the OAuth 2.0 Resource Owner Password Credentials (RPOC) grant authentication protocol.
Please note that the appliance should have access to the public internet for this mode to operate correctly. The network diagram will look like below.
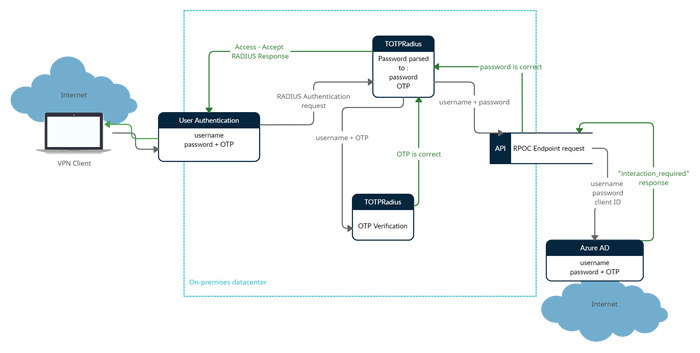
The password supplied by the user is expected to contain both the Azure AD (Microsoft Entra ID) password and the 6 digits OTP. The supplied password is parsed and the OTP gets verified locally and AD password is checked via Azure AD (Microsoft Entra ID) using the RPOC method.
The ROPC flow is a single request: it sends the client identification and user's credentials to the IDP, and then receives tokens in return. The client must request the user's email address (UPN) and password before doing so. In case the user account is protected with any form of MFA, the expected results returned by the OAuth2.0 endpoint is :
if the correct password is supplied:
{"error":"interaction_required"...if the supplied password is wrong:
{"error":"invalid_grant"...{
"token_type": "Bearer",
"scope": "User.Read profile openid email",
........
Please note that these types of users are not supported for security reasons. Only MFA-Enabled users can connect using the Azure AD (Microsoft Entra ID) Proxy mode.
In case the RPOC responds with "interaction_required", the authentication flow continues and if the OTP supplied is correct as well, a RADIUS response packet will be sent allowing the authentication.
Restrictions
With Azure AD (Microsoft Entra ID) Proxy mode only the primary factor (password) is verified against the Azure AD (Microsoft Entra ID) user records, the second factor is checked against the TOTPRadius local database only. The second factor supported is TOTP only, with fallback mechanisms such as SMS and Email. Please note that the fallback mechanisms are not recommended being used in production and there is no push notification possible.
The TOTP secrets imported in TOTPRadius can be the same as with Azure MFA - this will allow the users to use the same TOTP App profile or hardware token for TOTPRadius-connected authentication and Azure applications. You can also use a different set of TOTP secrets for TOTPRadius-hosted user records - in some scenarios this can enhance security even further.
Configuration
Follow the instructions below to configure your TOTPRadius in Azure AD (Microsoft Entra ID) Proxy mode. Before proceeding with the settings of TOTPRadius, you need to create an app registration within Azure.
Configure the OAuth Resource in Azure AD (Microsoft Entra ID)
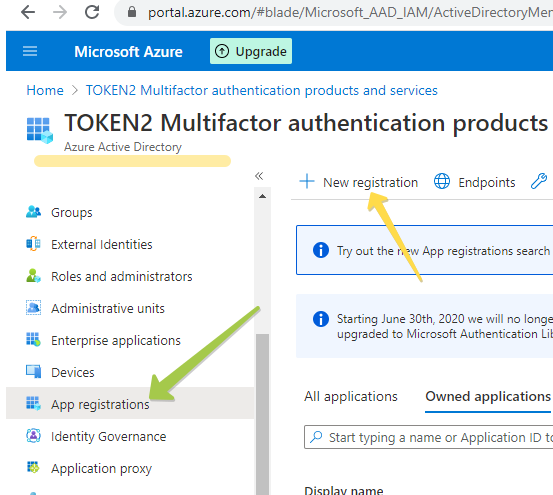
1. Navigate to the Microsoft Azure Portal and authenticate.
2. Navigate to Azure Active Directory.
3. Click on App Registrations.
4. Click on New Registration.
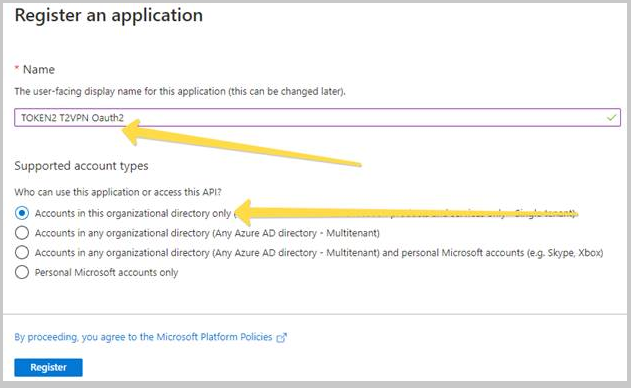
In the New Registration dialog, fill the form as shown on the example below, and click on “Register” to complete the action
After the App Registration is done, the Overview of the object will be shown (see example below).
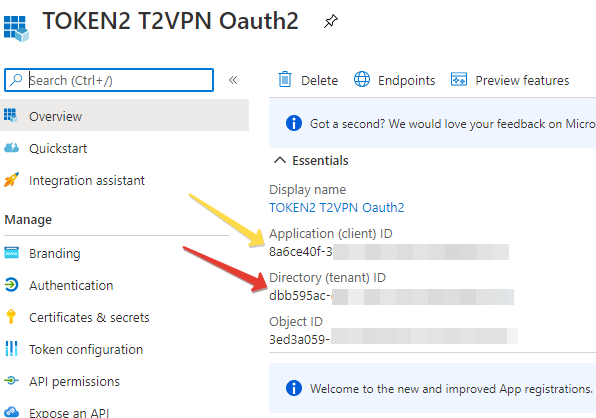
Note down the 2 IDs shown on this page (this can be retrieved at a later stage as well):
- Application (client) ID
- Directory (tenant) ID
These values will be entered into the TOTPRadius configuration settings in the next steps.
Configure TOTPRadius for Azure AD (Microsoft Entra ID) proxy mode
Login to the admin panel of TOTPRadius and navigate to the setting page ('Settings' button on the main page, or Settings → General settings from the header menu)
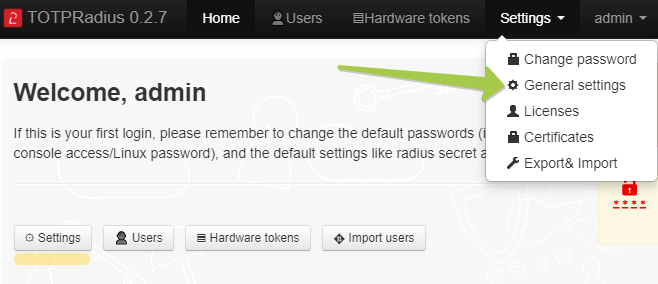
Navigate to Azure Active Directory Proxy section and set the parameters as shown in the example below:
Azure AD (Microsoft Entra ID) Proxy - Set 'Enabled'
Tenant ID and Client ID - Set to the values generated and recorded in the previous step
Azure AD (Microsoft Entra ID) domain - Set to the main domain of your Office365 tenant . This value will be used to convert regular usernames to full UPN when TOTPRadius is used with systems not supporting UPN as the username. For such systems, the username will be converted as in the example below:
username → username@token2.ch
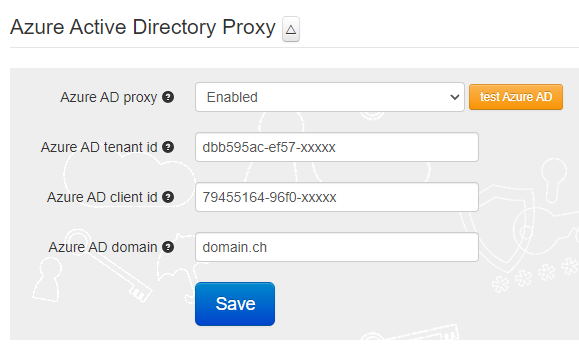
To make sure the configuration is correct, you can use the 'test Azure AD (Microsoft Entra ID)' button.
Provisioning the second factor in TOTPRadius
Due to technical limitations, only the primary factor (username+password) will be verified against Azure AD (Microsoft Entra ID) in this mode. The second factor (TOTP Secret) has to be provisioned independently for each user. This can be done via the admin panel as illustrated below:
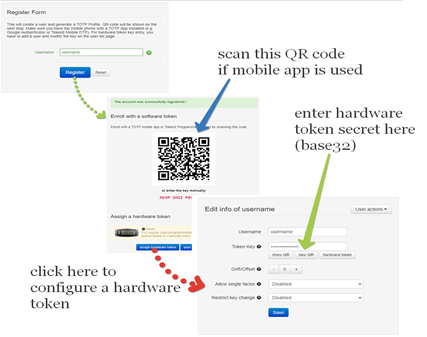
Reusing hardware tokens from Azure MFA
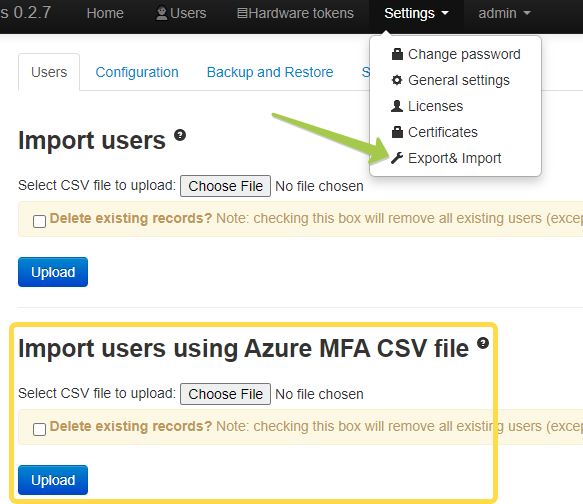
If you have Azure AD (Microsoft Entra ID) Premium P1 or P2 and use OATH Tokens functionality of Azure AD (Microsoft Entra ID), you can import the same csv file to TOTPRadius. This will allow your users to use the same hardware token for both Office365 apps and TOTPRadius-protected systems.
To import users from Azure MFA CSV file, navigate to Settings → Export&Import and upload the csv file in 'Import users using Azure MFA CSV file' section
Troubleshooting
If you encounter an error like the one below in the Azure AD (Microsoft Entra ID) test tool, it could be due to one of the following reasons:
1. The password provided is incorrect.
2. Azure MFA has not been activated for the user.
3. The Azure AD (Microsoft Entra ID) tenant ID or client ID is incorrect.
To identify the issue using logs, monitoring should be done from the Azure portal under Monitoring > Sign-in logs.
About
Installation and configuration
- Installation and initial configuration
- Network configuration
- Migrating from older versions
- LDAP Configuration
- Azure AD Configuration
- Self-service enrollment portal
- Web and LDAPS Certificates
- Syslog configuration
- Single-factor authentication exceptions
- Slave appliance mode
- Dynamic RADIUS Attributes
Integration guides
Blog
05-03-2026
Introducing TOTPVault — self-hosted TOTP management for teams
 Most TOTP apps work by distributing copies of the secret to every person who needs access — fine for personal accounts, but for shared service accounts it means MFA secrets scattered across people's phones with no clean way to revoke access when someone leaves.
Most TOTP apps work by distributing copies of the secret to every person who needs access — fine for personal accounts, but for shared service accounts it means MFA secrets scattered across people's phones with no clean way to revoke access when someone leaves.
21-12-2025
Android, NFC, and the Missing Piece of WebAuthn
 For years, Android users have faced a frustrating limitation—Android does not support CTAP2 over NFC. This means no PIN verification and no discoverable credentials (passkeys) when using NFC, and therefore limited to simple U2F-style flows without user verification. That said, there finally seems to be a solution.
For years, Android users have faced a frustrating limitation—Android does not support CTAP2 over NFC. This means no PIN verification and no discoverable credentials (passkeys) when using NFC, and therefore limited to simple U2F-style flows without user verification. That said, there finally seems to be a solution.
19-12-2025
Streamline Token2 Classic Tokens in Okta
 Token2 classic hardware tokens provide phishing-resistant multi-factor authentication for your Okta environment. Our updated integration guide shows you how to deploy them using Okta's Custom OTP authenticator method.
Token2 classic hardware tokens provide phishing-resistant multi-factor authentication for your Okta environment. Our updated integration guide shows you how to deploy them using Okta's Custom OTP authenticator method.